https://osalbishri.wordpress.com/2016/11/27/government-surveillance/comment-page-1/#comment-79
https://mangrumnewmedia.wordpress.com/2016/11/28/government-surveillance/comment-page-1/#comment-78
I wrote about one man’s crowdsourcing project to create a map of bike routes in a city overrun by cars (Malaysia’s capital Kuala Lumpur). Jeffrey Lim, told The Guardian, he handed out blank maps to volunteers and asked them to explore anywhere “from major roads to unmarked paths” to find potential cycling routes.
The finish product resulted in 10,000 cycling maps, in three languages, that he distributed in the capital. Lim also received an invitation from the Kuala Lumpur mayor to expand and fine tune the project.
I loved the creativity of this project, where private individuals worked together to create a bike infrastructure when there was nothing. Crowdsourcing was essential to this project because by having many people draw their own map you solve a problem through “unique perspectives and internal heuristics” (Brabham, p. 308)
Intrinsic motivation, as Daren Brabham writes about, explains why so many people participated in the grassroots project. Lim says more than 50 volunteers started to appear each week during meetings at his studio. The cycling community seemed motivated to connect with fellow bicyclists, share knowledge and solve the problem itself (p. 315).
The bike map differed from Next Stop Design in that it wasn’t a competition. Everyone was working on the same map, and that likely reduced or eliminated extrinsic motivation. Perhaps, Lim eventually felt an extrinsic motivation when the successful project started getting attention from the government. However, it would be unfair to say that was a primary motivation.
Creating a shared, safe bike path and improving biking conditions in the city were “rational motivators.” The chance to “contribute to a collaborative effort” (“norm-based”) and have fun (“affective”) could additionally be seen as motivators. (Brabham, p. 320).
The cycling map had less in common with Gregory Asmolov’s crowdsourcing project. The bike route map and Next Stop Design use crowdsourcing to build something that wasn’t there before. In the emergency response case, you’re taking an online system that’s already in place — platforms for alerting people during an emergency — and using crowdsourcing to improve the accuracy and efficiency of it. Asmolov looks at improving known tools (“tool mediation”) to enhance the relationship between the subject and object/disaster (p. 3).
Still, there are parallels. Both projects require you to inform, alert and engage potential participants. A cyclist or emergency respondent can merely consume alerts or act “as a potential contributor of information” and engage (Asmolov, p. 12).
There’s a clearer power relationship at play in Asmolov’s crowdsourcing example however. The cycling example is more open-ended — turning a blank paper into a map. In the emergency responder project, you’re trying to improve a system/technology that already exists, thus you must work within the framework of that system/technology. If the framework isn’t good in the first place, crowdsourcing a productive result will be difficult.
Both readings this week examine the way mobile phones are used in low-income countries. Each author takes a skeptical look at the way mobile tech can bridge the digital divide (Wijetunka, p. 712) or bring about social change (Wasserman, p. 148). The ability of mobile phones to create positive influence is seen as too simple and technological deterministic to apply across the board to low-income countries, despite cheap access to the devices.
New technology did have positive effects in communities with significant mobile penetration, but research showed that access still can exacerbate digital divide since phones are designed with affordances that are only understood by privileged groups. Wijietunka discusses the way inequalities are built into phones in Sri Lanka when they’re designed for youth who “have previously engaged in with the use of computers (p. 719).
Wasserman looks at inequalities in a separate but similar way. In his example as well, underprivileged peoples cannot use a phone to its full usage. However, in this case it’s because of prohibitive costs (subscriber rates, owning chargers) of using the phones (p. 149).
Mobile tech is used more to “full capacity” by governmental organizations and privileged people. Underprivileged groups in both articles mainly use phones for talk and text — passive usage (Wasserman, p. 154).
Wijietunka’s focus group interviews only looks at the inequalities built into phones. Wasserman’s analysis shows how underprivileged groups can overcome those inequalities through creative means and “transgressions.” There are informal economy in parts of Africa centered on cellphone technology use. Wijetunka hints at transgressions by saying Sri Lankan underprivileged youth sometimes take extra steps to overcome areas where they lack cultural capital/competency (p. 722).
Part 2:
I would like to design a study about the mobile Internet and undocumented immigration in the U.S. Mobile technology has changed the way we communicate, and studies already show U.S. Latinos use mobile more than other similar demographics. My study would survey undocumented immigrants/refugees in South Florida who are young adults (ages 18-34) that identify as Hispanic/Latino ethnicity and own mobile devices.
My first research question would compare mobile usage between immigrants from low-income (Honduras, El Salvador, etc) and medium-income countries (Venezuela, Colombia) in Latin America, using GDP per capita as a guide.
1) How do immigrants from countries with higher GDPs use mobile technology different than immigrants from countries with lower GDPs?
My second question would be on how undocumented immigrants to create identity while living in a new country.
2) How do Latino immigrants use mobile technology — through apps and interpersonal communication — to define themselves?
These questions would aid immigration studies by showing the disparities between the ways undocumented immigrants use their mobile phones, and whether immigrants from more “privileged” (according to GDP) backgrounds use phones more to full capacity (Wijetunga, p. 713). NGOs could use this information to better train new immigrants on how to use affordable mobile technology in their lives. NGOs and news media could use the second question to understand informal networks (a version of “radio trottoir”) and how they communicate and receive information and satisfy personal and cultural needs.
Welp, forgot about these before my class field trip today. But these were really great and I wanted to comment about them, and what the hey it’s Friday night, so why not:
https://irene8787.wordpress.com/2016/10/31/remix-an-agent-couple/comment-page-1/#comment-51
https://liandralarsenblog.wordpress.com/2016/10/30/trump-remix/#comment-47
In his paper on hackers, Johan Söderberg delves into the concept of “technological determinism.” The concept says that new technology should be seen as progress and bring about inevitable change. Söderberg brings up a concern “held by social scientists that a belief in technological determinism rules out popular, political engagement” and favors elites (p. 1289).
The reasons this belief sounds problematic become readily apparent from that framework. Not all technology will catch on. So “technological determinism” claims you’re delaying the inevitable when that is not always the case. Nor will technology necessarily bring about positive change, and so it’s fair to ask: Are all technological breakthroughs “progress”? Think of how a new technology can favor people in power who have access (or investments) in that product. By claiming “technological determinism,” the people in charge are saying accept this new product. Do not challenge it. This doesn’t leave room for dissent or regulation and clearly hurts democracy.
I think of concerns about AI, when thinking about how “technological determinism” hinders democracy and can setback progress. You can’t simply let technology run rampant without any type of oversight because this “advanced” technology court hurt society. In fact, “The Terminator” movies seem to use “technological determinism” as a running theme. The AI known as Skynet will destroy society no matter what barriers are put in its way. But if we allow for “indeterminacy” that means change or progress can come from elsewhere and we need democratic processes to allow for that.

Nicholas John, in his academic paper on “file sharing,” quotes legal scholar Jessica Litman who says, “Sharing digital objects is less like sharing cookies she claims, and more like sharing ideas — when I share my ideas, I don’t lose anything” (p. 201). This refers to the concept of rival and non-rivalrous goods.
Non-rival goods can be shared by more than one person at a time without the product diminishing. The example given by seemingly every source (for example, this one) is National Defense. Furthermore, a non-rivalrous product like defense becomes a public good when it can be shared without excluding anyone. A rival good is an item that only can be consumed or used by one person at a time. To share a rival good comes with the knowledge that you’ll lose it or at the very least have less of it than you did before, like giving someone a slice of your pizza.
There’s an implicit connection between non-rival and rival goods in sharing. A simple calculation must be made with rival goods: Can you afford to lose it? Non-rival goods remind me of our discussions of the public sphere. A non-rival good — since the cost is shared and the supply is unlimited — becomes a question of do you want more people to have this? Anyone can communicate freely in a society if free speech rights extend to all citizens. But a government can restrict this non-rivalrous good. The calculations involve more complex ideas and pertain to ethics and power.
Updated Wednesday to add comic on “technological determinism”
Social media rules the web and everyone is looking to “go viral.” How do you define virality and how do we achieve it? I created a Storify that looks at five key lessons about what it means to go viral.
Longtime Miami Herald columnist Andres Oppenheimer wrote about the “Biggest test to U.S.-Cuba talks: The Internet.” He argues that the Obama Administration needs to push Internet access in diplomatic talks with Cuba to make re-establishing ties with the Communist regime meaningful.
Oppenheimer notes that the Internet penetration rate in Cuba is “one of the lowest in the world. Only 5 percent of Cubans have access to unrestricted Internet.” The Cuban government lets citizens access a “heavily-censored Intranet” filled with propaganda. Most of the island is kept in the dark “about the outside world, and about what’s going on inside the island.”
The column’s implication — that unfettered Internet access can help open up Cuba’s political system — complements Shirky’s article on “The Political Power of Social Media.” The cuban government maintains a monopoly on public speech. By providing communication tools and better Internet access to citizens, a public sphere for conversation can develop and in turn dissident movements can clandestinely form.
This is Shirky’s “environmental view of Internet freedom.” The goal here is not to stir dissent through Western propaganda or recruit rebels for another “Bay of Pigs.” This view recognizes that protests come “at the end of a long process.” The objective is simply to create an online space where many conversations can occur (Shirky, 2011). Eventually that should include dissident activity. When it does it’ll be harder to shut down because turning off the Internet would upset not only dissidents but everyone using the public sphere (Shirky refers to this as the “dictator’s dilemma” or “conservative dilemma”).
Oppenheimer implores Obama to keep plans to “make increased U.S. exports of Internet equipment and services a key part of his normalization talks with Havana.” The author never mentions anything like democratization or opposition movements. There seems to be a tacit acknowledgement that authoritarian regime change happens slowly and cannot be forced, just as Shirky notes.
After more than 50 years in power, few would believe the ruling party in Cuba is on the verge of collapse. But by giving Cubans private communication tools like smartphones, citizens could eventually echo likeminded anti-Castro opinions and coordinate against the Communist regime.
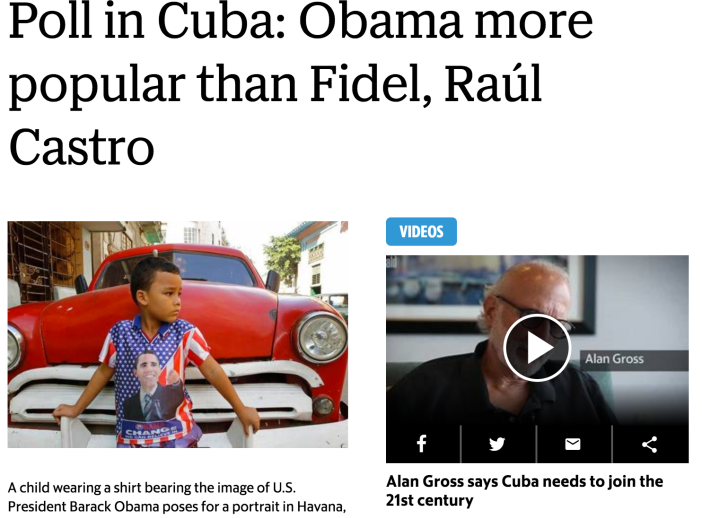
Oppenheimer’s column has less overlap with Conor and Bean’s article on public diplomacy through “engagement.” Their piece examines how the U.S. can use the Internet and social media to win over skeptical audiences in foreign countries. Most Cubans, however, have a positive opinion of the U.S. and overwhelmingly support re-establishing ties. A secret, comprehensive poll conducted in Cuba last year resulted in headlines like “Obama more popular than Fidel, Raúl Castro.”
Still, the administration could hurt its cause if diplomats promote solely “Brand Obama” over “genuine” engagement (p. 212) . The Cuban public are largely dissatisfied with their government. An open dialogue with the Cuban government must go beyond the Castros’ priorities of “tourism, oil, renewable energies, biotechnology and food” to honest (but not bullying) discussions of Internet access. Else talks could ring hollow with Cubans (both in the U.S. and the homeland).
Screenshot – Miami Herald:
My viral story is on Boaty McBoatface (via The Guardian), the winner of a poll by a British governmental entity to name a new ship.
In the spring of 2016, RSS Boaty McBoatface received almost 125,000 votes and crushed more solemn contest options. The goofy story gained worldwide attention. Would the United Kingdom’s Natural Environment Research Council actually name one of its vessels Boaty McBoatface?
No. They snubbed democracy (or Internet mob rule) and christened the ship the RSS David Attenborough, which received the fifth-most votes. Nevertheless, by that point Boaty McBoatface had been aggregated by major news sites, used as late-night talk show fodder and inserted into weird thinkpieces.
[Video: U.S. Senator Lindsey Graham liked the name Boaty Mac]
Alhabash & McAlister (2015) note that we are “cognitive misers” and more likely to share the “least cognitively demanding” posts (p. 1,321). There’s not much to think about with Boaty McBoatface. It’s an ill-fitting name for a government research ship, and the experience feels disruptive and fun. Facebook and Twitter users like the social media sites primarily for “entertainment”, according to Alhabash and McAlister. Boaty McBoatface fits that bill. Another top motivation for engaging with social media was “information sharing” — and this viral ship was part of a real news event (p. 1,323).
Alhabash and McAlister suggest vaguely that “personalized, tailored and medium-specific” social media campaigns are practical for companies and non-profit organizations (p. 1332). This advice seemed rather lax and incomplete. They don’t acknowledge the lack of control businesses have over social media. Viral brand stories can happen when something unplanned, and sometimes unwanted, happens à la Boaty McBoatface. The research paper gives the example of a create your own Ford Mustang Facebook application as a successful idea. Yet a similar attempt centered on Chevy Tahoes backfired.
We’re driven to share stories that physiologically arouse us (Berger and Milkman, p. 193). Positive stories, especially amusing ones like Boaty McBoatface, tend to get shared more (p. 200). We felt awed by the contest results too. Those feelings of excitement improve “virality.” What seems to be missing from the Berger and Milkman study is how a sense of camaraderie boosts viral stories. Even if we didn’t vote, by sharing the story we felt a part of it. We all were rooting for Boaty McBoatface. I hypothesize the duration of the contest helped the story’s reach because we felt involved in the outcome. People felt “deactivated” (stopped sharing as much) once the ship officially received its boring, new name (p. 201).
Users needed to corrupt the vote to create virality. Once “Boaty McBoatface” emerged as the preferred choice, we could explain why using Jonah Peretti’s ways to go viral. The story had a heart, a silly and shareable identity and a sense of humor. Internet users have hijacked online contests before. But other instances have been too vulgar or obscure to reach these viral heights.
In this case, most anyone could appreciate the simple genius of Boaty McBoatface.
I’d explain algorithms to a young child by pointing to their school teacher — and the way they try to understand you. A teacher might not know you well at the beginning but as the school year progresses and the teacher has more knowledge (data) about the child, they can start catering better to his or her interests.
They can suggest relatable books or movies or keep a child away from food that he or she is allergic to. The longer the teacher knows the child the better the instructor can assist the 8-year-old. But that also depends on how adept the teacher is in understanding the student and also, sometimes despite the teacher’s understandings, some suggestions might still be way off. It happens. Nobody’s perfect and neither are algorithms.
I’m not an active user of Reddit, but I visit the front page on a daily basis. Since I don’t have an account and mainly look at links on the first few pages, the content I see are the most popular results from the Reddit algorithm — a formula primarily influenced by upvotes and downvotes from the site’s users. In this case, it’s a user base that’s heavily white, male and in their teens or early 20s. It shows. Internet savvy users and the crowdsourcing formula put soon-to-be-viral videos on Reddit first. Adorable animal gifs abound.
I rarely read breaking news there first. The algorithm/voters do not like controversy. Political news like the New York Times’ reveal of Donald Trump’s tax returns did not make waves on the homepage (an innocuous SNL skit on the debate did). Stories pertaining to national issues concerning women or minorities almost never make the front page. Stories vilifying them will. Weirdly, the site’s anti-authoritarian streak means I’ll see supportive posts about Black Lives Matter and police brutality. At the same time, race-baiting anti-BLM stories about riot damage after a police shooting will be gleefully upvoted to the top. Site users exhibit a stunning lack of media literacy, and the algorithm can’t keep hoax stories from the front pages. Reddit users hate things that are politicized. But as a result site’s “hivemind” has by-accident built an algorithm that’s highly politicized, blind to its own biases and often grotesque.
In regards to Crawford’s third example, I once worked for a news/travel site where we almost entered into an agreement with an advertiser where we would try to scam Google SEO (by ignoring nofollow links). Ultimately we decided against it since Google’s algorithm will punish/blacklist anyone caught gaming the system. However it’s hard for smaller sites to compete when Google results often promote powerful sources with their own issues like TripAdvisor, Wikipedia or content-farmed listicles.
Google PageRank doesn’t combat hoaxes either. Search for “sharia law Texas” or “sharia law in the U.S.” and you’ll get a bunch of conservative or alt-right sites in the results — with sometimes only Snopes beating back the lies. I once took advantage of the algorithm to publish a story explaining how the “sharia law in Texas” hoax started (2nd result below). But if mainstream media aren’t writing about a popular conservative issue, fact-free search results proliferate.
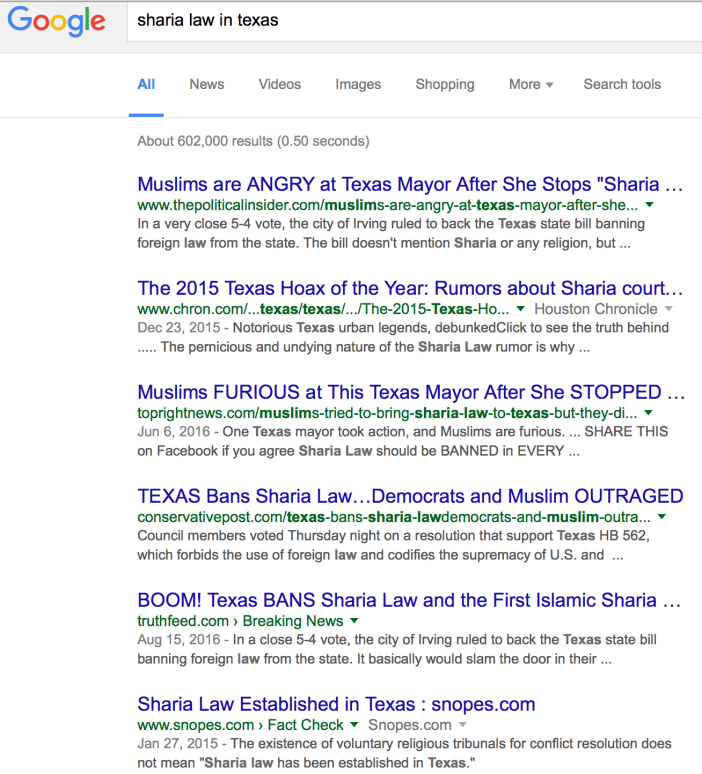
(Texas couldn’t ban Sharia Law since foreign laws aren’t legal in the first place).
I looked at the Privacy Policy for Deadspin and by association the Gizmodo Media Group. This is the news site I visit most regularly without going through social media (though I visit less often since the demise of Gawker).
I have signed up for a commenting account that I rarely use and will occasionally click on the Deadspin links to affiliate sites or share articles via social media. So how much is my privacy at risk?
Just by clicking links or signing up for an account, I’m setting myself up for specific serves from third parties and having my demographic information sold to advertisers. I probably have acknowledged passively that this was taking place. But I never thought about it much despite my concerns for privacy.
In other words, I contribute to the “privacy paradox” that Taddicken brings up (Taddicken, 2014). However, I can’t say I was bothered by much of what I found. I say I’m concerned about privacy but not feel like I’m in control of what I disclose whether it’s thoughts, feelings or my email address.
The most troublesome item in the privacy policy is how if the company is bought, your information likely will be transferred to the new company whoever that is. So in this case, Univision now has access to whatever previous info I had given the Gizmodo sites. It provides more perspective on why a company like Verizon would spend almost $5 billion on a money sinkhole like Yahoo — for the user data. I don’t like that a telecommunication company can get my data simply because they have the money. But as the Ted Talks: Kovacs points out behavior tracking is now a billion dollar business that makes it even easier for companies to get our personal data (Kovacs 2012). Disturbing.
I’ve primarily thought of privacy in terms of personal privacy (which protects me) and not corporate privacy (which protects business interests). So I found Fuchs’ insights to be eye-opening. It’s easy to get people fired up over personal privacy. But it seems like corporate privacy — and the way social media platforms like Facebook use our data — should be a much bigger issue. Gizmodo Media Group too commodifies and sells user data to third-party advertisers. Plus, site visitors are “prosumers” who help create content for the site either via commenting or send in tips, which helps enrich the site. (Fuchs, 2012)
I’m not against all this. I think for a media site to exist (a fourth wall) in society they need to privately be able to make money and be capable of paying for expenses that ensure solid reporting, fact-checking, etc. (I don’t think Fuchs suggestion of alternative Internet platforms are realistic for news media sites; perhaps for social media)
But I do appreciate transparency on how my data and self-disclosures will be used. The most interesting bit of information I found in the private policy was a link to aboutads.info that detects all the “companies customizing ads for your browser.”
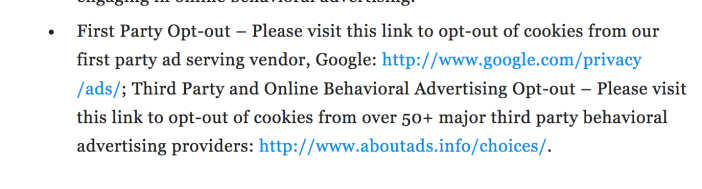
Currently, the Digital Advertising Alliance detects 33 companies, and I could choose to opt out of them in one step. I’m not sure if I want to do this yet (do I really prefer ads that don’t target me?). Still, even this is not the opt in “positive indication” that’s discussed in Fuchs’ socialist conception of privacy, it seems this type of opt-out transparency and watchdog-ing is a good step for web users.